This guide navigates the intricate world of computer networks, offering valuable insights for everyone from novice users to seasoned professionals. Whether you’re a network administrator, business owner, educator, or simply curious about the digital realm, this resource provides a practical understanding of network fundamentals, emerging technologies, and essential security practices.
Building Blocks: Network Topologies and Architectures
Network topologies are the architectural blueprints of your network, dictating how devices interconnect and communicate. Selecting the correct topology is paramount for optimal performance, scalability, and security.
Exploring Common Topologies
Star Topology: Like a bicycle wheel, devices connect to a central hub (e.g., router or switch). This common setup in homes and small offices offers simplified management and isolates device failures. However, the central hub becomes a single point of failure. Consider redundancy for critical networks.
Bus Topology: Resembling a single highway, all devices share a single cable. While simple and cost-effective, a cable break disrupts the entire network. This vulnerability limits its use in modern networks.
Ring Topology: Data flows unidirectionally in a closed loop, passing through each device. This topology offers efficient data transfer, but a single device failure can impact the entire network. Redundant rings can mitigate this risk.
Mesh Topology: Like an interconnected web, multiple paths exist between devices. This redundancy ensures high reliability and fault tolerance. Mesh networks are common in critical infrastructure and large enterprise environments due to their robustness but increased complexity.
Tree Topology: A hierarchical structure combining elements of bus and star topologies. It organizes networks into branches, allowing for scalability and segmented management. However, failures at higher levels can affect multiple branches.
Choosing the right topology requires careful consideration of network needs, scalability requirements, and budget constraints.
IP Addressing: The Language of Networks
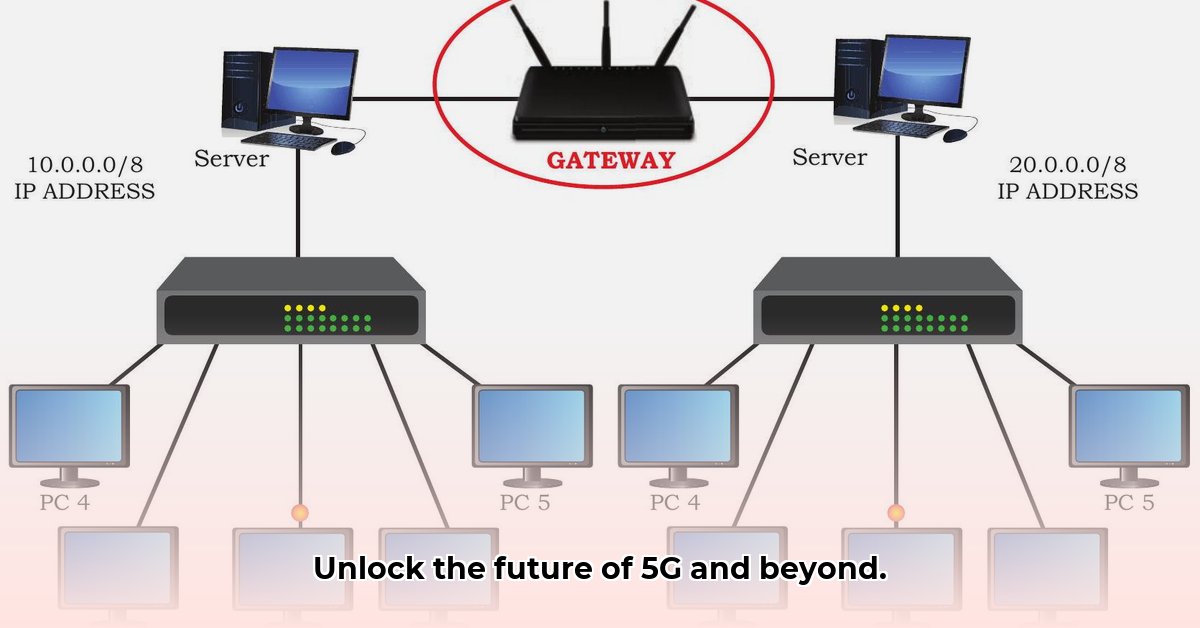
Every device on a network requires a unique identifier, much like a postal address. This is the role of IP addresses.
IPv4 and IPv6: Addressing the Future
The internet primarily uses IPv4, a 32-bit addressing scheme. However, the exponential growth of connected devices has led to address exhaustion. IPv6, a 128-bit addressing system, provides a vastly larger address pool to accommodate the expanding Internet of Things (IoT) and future network growth. Transitioning to IPv6 is crucial for long-term scalability and seamless connectivity.
Network Security: Shielding Your Digital Assets
Protecting your network from cyber threats is paramount. A multi-layered security approach is essential.
Essential Security Practices
Firewalls: These gatekeepers filter incoming and outgoing network traffic based on predefined rules, blocking unauthorized access and malicious activity. Implement both hardware and software firewalls for comprehensive protection.
Intrusion Detection/Prevention Systems (IDS/IPS): These vigilant systems monitor network traffic for suspicious patterns, alerting administrators to potential threats and even actively blocking malicious traffic.
Virtual Private Networks (VPNs): VPNs create secure, encrypted connections over public networks, safeguarding sensitive data during transmission and providing anonymity.
Multi-Factor Authentication (MFA): MFA adds an extra layer of security by requiring multiple forms of verification, such as passwords, biometrics, or one-time codes.
Regular Security Audits and Updates: Conduct regular security assessments to identify vulnerabilities and ensure software and firmware are up-to-date with the latest security patches. Implement robust security protocols and educate users on best practices.
Wireless Networking: Embracing Mobility and 5G
Wireless technologies like Wi-Fi and 5G have revolutionized connectivity, offering seamless mobility and high-speed data access.
5G and Beyond: The Next Generation
5G delivers significantly faster speeds, lower latency, and increased capacity compared to its predecessors, enabling new applications like autonomous vehicles, augmented reality, and smart cities. However, the increased complexity of 5G networks introduces new security challenges. Robust security measures are crucial to protect data on these high-speed networks. Research and implement 5G security best practices to mitigate potential risks.
Network Virtualization and Software-Defined Networking (SDN): Transforming Network Management
Network virtualization creates multiple, isolated virtual networks within a single physical infrastructure, optimizing resource utilization and enhancing flexibility. SDN centralizes network control, enabling dynamic configuration and automated management. These technologies are transforming network management and driving innovation.
Embracing the Future of Networking
SDN and network virtualization offer increased agility, scalability, and cost-efficiency. They enable businesses to adapt their networks rapidly to changing demands and optimize performance. Explore and implement SDN and virtualization solutions to modernize your network infrastructure.
Actionable Steps: Taking Control of Your Network
Comprehensive Network Assessment: Analyze your current network infrastructure, identify vulnerabilities and areas for improvement. Conduct thorough audits to evaluate performance and security.
Strengthening Security Posture: Implement a multi-layered security approach, including firewalls, IDS/IPS, VPNs, MFA, and regular security updates.
Future-Proofing Your Network: Plan for future growth and scalability by adopting technologies like IPv6, 5G, SDN, and network virtualization.
Continuous Performance Monitoring: Implement network monitoring tools to track performance metrics, identify bottlenecks, and address issues proactively.
Staying Informed and Educated: The networking landscape is constantly evolving. Stay updated on the latest technologies, security threats, and best practices through continuous learning and professional development.
By taking these steps and embracing a proactive approach, you can master the complexities of modern computer networks and navigate the ever-evolving digital world.
- Amazing March Fun Facts: Unveiling History & Celebrations - April 15, 2025
- Master how to write height: A complete guide - April 15, 2025
- How High Are Your Standards Test: Find Your Perfect Match Now - April 15, 2025